Cryptoviruses and Ransomware
Were there a ranking for the most dangerous and show-stopping malware, the various types of Ransomware, and especially Cryptoviruses, would top the list. Imagine this scenario:
You’re browsing the internet, maybe watching a Youtube video, checking Facebook, playing a game, or maybe even reading some Emails, when a program pops up telling you that it’s time to update an innocuous program such as Adobe Flash Player. You think to yourself, “Sure, Flash is pretty important, I’ll update it.”
You continue going about your business when suddenly, your computer locks up and a window like this appears.
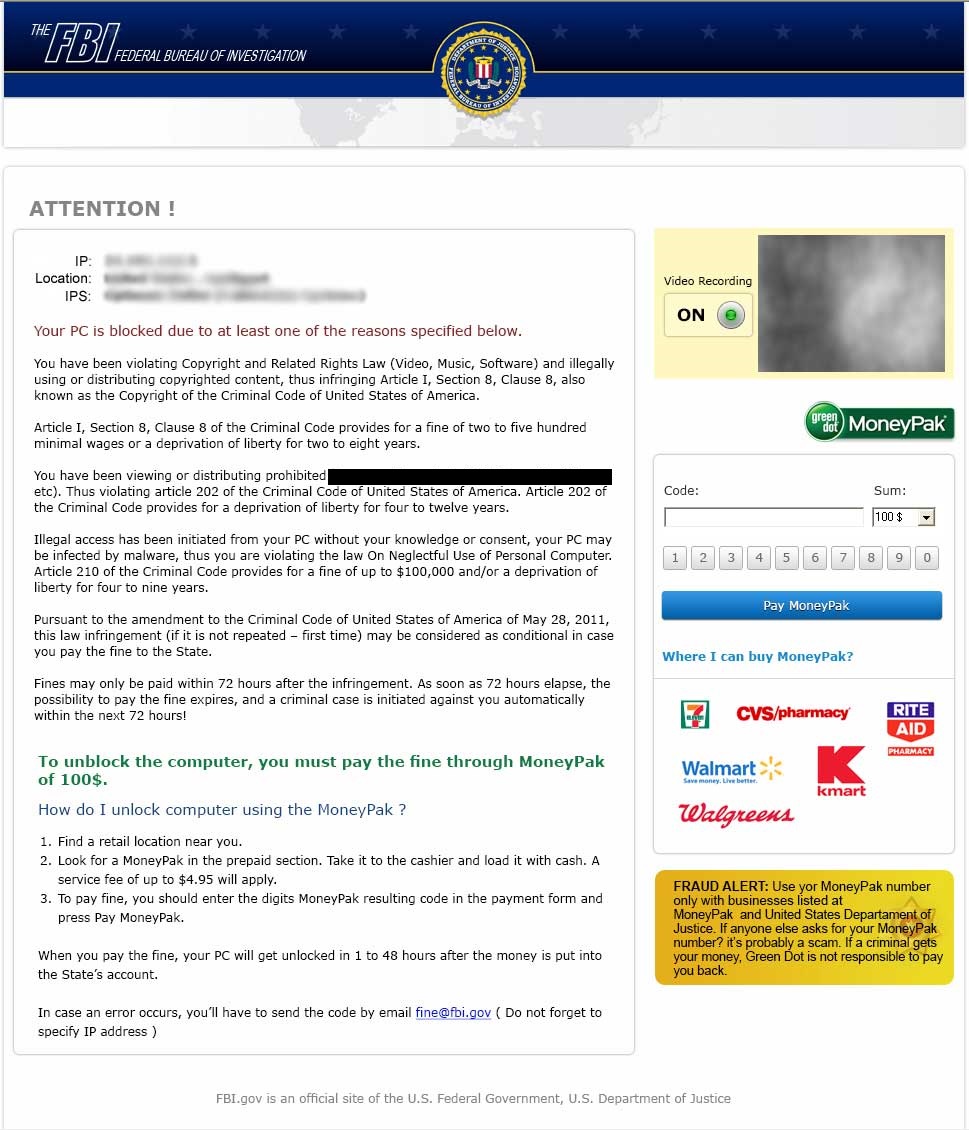
Now, to most people, this will be pretty jarring. As if the accusations were not startling enough, the page also turns on the user’s webcam and displays a live video feed, as if collecting video evidence. However, the page is a clever ruse designed to convince users that the FBI (or some other government organization) believes that they are guilty of a crime and requires them to pay a fine to avoid criminal charges or jail time. Rebooting the computer does not solve the problem, as the virus starts with the afflicted computer. The computer remains locked until the “fine” is paid, and in some cases paying might not even unlock the computer. Now, this type of virus is much more invasive and troublesome to defeat than most, and even harder to avoid. However, in most cases, an experienced technician can find a way around it, so that it can be removed.
CryptoLocker, CryptoWall, and other Encryption Viruses
On the by and large, Ransomware can usually be defeated in relative brevity by technicians with the proper set of knowledge and tools at their disposal. But what happens if the virus does more than just lock up your computer?
A Cryptovirus is one type of Ransomware that not only locks up the user’s computer, but encrypts all the user’s data as well. When the data (which can range from pictures to Word documents to AutoCAD work files) is encrypted, it becomes unreadable and inaccessible unless the person trying to open the files has the decryption key. This can be pretty problematic, as even if the virus is removed, the data will remain encrypted.
What Can Be Done?
Most of these dangerous programs encrypt the files of the victim’s computer with a heavier encryption than the average bank, so trying to crack it is not only unfeasible, but practically impossible.
If the files are of little consequence or not worth the effort, then your technician can remove the virus and get the computer working again, but the data could be lost forever. Occasionally, the good men and women of the various cybercrimes divisions in agencies such as the FBI, Interpol, or alternatively, the employees of various companies specializing in data security, expose a vulnerability in the encryption or manage to obtain a set of decryption keys with which previously encrypted files could be returned to normal.
The first version of CryptoLocker was shut down in a joint effort in such a way, and one of the parties managed to obtain the decryption keys so that victims of this attack were able to unlock their data. As such, if you would appreciate the possibility of eventually getting your data back, speak with your technician about saving the encrypted data somewhere long-term, as the potential for this to happen again exists.
There is also the option of paying the ransom, however such a prospect is usually expensive (in the order of several hundred dollars) and is not guaranteed to work. In addition to this, if one chooses to pay, it can be difficult even to execute such a payment as often the virus maker will request Bitcoin, or some other form of anonymous cryptocurrency, which can be difficult to acquire and transfer. There is also the distinct possibility that any ransom paid could go to the funding of either terrorist organizations, or at the very least, supporting such cyberattacks in the future.
Prevention and Safeguards
Unfortunately, at the present time, the best way to deal with this type of threat is not to run into it at all. Keeping an up to date antivirus, maintaining good browsing habits, and always reading the screen before you click “accept” should improve your chances.
Preferably, an antivirus providing real time protection should be considered, since these types of viruses are the types that need to be stopped at the gate. Once they get in, it could very well be too late.
Besides this, data backup is paramount. There is no such thing as a perfect defense, and when something does get through and wreak havoc, you will want to know that your data is safe. In some cases, even data backups can be affected, so it’s good to use your local technicians as resources to finding the best strategy for your situation.
Related posts: Escaping the Fake Blue Screen Popups and Evading Similar Scareware, Revisiting the Fake Blue Screen and Virus Alert Popups
